2. Requirements
2.1. Hardware Requirements
There are a few things to consider, before you start with the installation.
If you install on VMWare, the minimum requirements for the virtual machine are as follows:
System memory: 16 GB
Hard disk: 200 GB
CPU cores: 2
The disk size of 200 GB is fine in scenarios where you import only Alerts and Warnings into the Cockpit, scan less than 1.000 systems on a weekly basis and want to keep the logs for less than one year. If you also import Notices and Info messages for these 1.000 servers, we recommend a disk size of at least 500 GB.
For an Installation of up to 20.000 endpoints the following specifications are recommended:
System memory: 32 GB
Hard disk: 2 TB SSD
CPU cores: 4
2.2. Network Requirements
The Analysis Cockpit and other systems which will have to communicate with each other, need the following ports opened within the network. For a detailed and up to date list of our update and licensing servers, please visit https://www.nextron-systems.com/hosts/.
The Analysis Cockpit requires the following open ports (incoming).
2.2.1. From Management Workstation to Analysis Cockpit
Description |
Ports |
|---|---|
Administrative Web Interface |
443/tcp |
Command Line Access |
22/tcp |
2.2.2. From Analyst Workstation to Analysis Cockpit
Description |
Ports |
|---|---|
Administrative Web Interface |
443/tcp |
2.2.3. From ASGARD Management Center to Analysis Cockpit
Description |
Ports |
|---|---|
Syslog Forwarding |
514/tcp, 514/udp |
Asset Synchronization |
7443/tcp |
2.2.4. From Analysis Cockpit to SIEM (optional)
Description |
Ports |
|---|---|
Syslog Forwarding |
514/tcp, 514/udp |
2.2.5. From Analysis Cockpit to the Internet
The Analysis Cockpit is configured to retrieve updates from the following URLs:
Analysis Cockpit packages: https://update3.nextron-systems.com
A proxy system should be configured to allow access to these URLs without TLS/SSL interception (Analysis Cockpit uses client-side SSL certificates for authentication). It is possible to configure a proxy server, username and password during the setup process of the Analysis Cockpit platform. It only supports BASIC authentication, not NTLM Authentication.
2.2.6. From Analysis Cockpit to Sandbox Systems (optional)
Depending on the Sandbox system and your individual configuration.
Description |
Ports |
|---|---|
Sandbox (typically) |
443/tcp, 8080/tcp |
2.2.7. Time Synchronization
Analysis Cockpit tries to reach the public Debian time servers by default.
Server |
Port |
|---|---|
0.debian.pool.ntp.org |
123/udp |
1.debian.pool.ntp.org |
123/udp |
2.debian.pool.ntp.org |
123/udp |
The NTP server configuration can be changed in the settings.
2.2.8. DNS
Analysis Cockpit needs to be able to resolve internal and external IP addresses.
Warning
Please make sure that you install your Analysis Cockpit with a
domain name (see Network Configuration).
If you do not set the domain name and install the ASGARD package,
you will have problems connecting your ASGARD(s) to the Analysis Cockpit.
All components you install should have a proper domain name configured to avoid issues further during the configuration.
2.3. Internet Access during Installation
The Analysis Cockpit installer requires Internet access during the setup. The installation process will fail if required packages cannot be loaded from https://update3.nextron-systems.com
2.3.1. SSL/TLS Interception
The installation and update processes do not accept an unknown but valid SSL/TLS certificate presented by an intercepting entity and therefore don't support SSL/TLS interception.
Since our products are usually used in possibly compromised environments, the integrity of our software and update packages has highest priority.
2.4. Verify the Downloaded ISO (Optional)
You can do a quick hash check to verify that the download was not corrupted. We recommend to verify the downloaded ISO's signature as this is the cryptographically sound method.
The hash and signature file are both part of the ZIP archive you download from our portal server.
2.4.1. Via Hash
Extract the ZIP and check the sha256 hash:
On Linux
user@unix:~/nextron-universal-installer$ sha256sum -c nextron-universal-installer.iso.sha256
nextron-universal-installer.iso: OK
or in Windows command prompt
C:\temp\nextron-universal-installer>type nextron-universal-installer.iso.sha256
efccb4df0a95aa8e562d42707cb5409b866bd5ae8071c4f05eec6a10778f354b nextron-universal-installer.iso
C:\temp\nextron-universal-installer>certutil -hashfile nextron-universal-installer.iso SHA256
SHA256 hash of nextron-universal-installer.iso:
efccb4df0a95aa8e562d42707cb5409b866bd5ae8071c4f05eec6a10778f354b
CertUtil: -hashfile command completed successfully.
or in Powershell
PS C:\temp\nextron-universal-installer>type .\nextron-universal-installer.iso.sha256
efccb4df0a95aa8e562d42707cb5409b866bd5ae8071c4f05eec6a10778f354b nextron-universal-installer.iso
PS C:\temp\nextron-universal-installer>Get-FileHash .\nextron-universal-installer.iso
Algorithm Hash Path
--------- ---- ----
SHA256 EFCCB4DF0A95AA8E562D42707CB5409B866BD5AE8071C4F05EEC6A10778F354B C:\Users\user\Desktop\asgard2-installer\nextron-universal-installer.iso
2.4.2. Via Signature (Recommended)
Extract the ZIP, download the public signature and verify the signed ISO:
On Linux
use@unix:~/temp$ wget https://www.nextron-systems.com/certs/codesign.pem
use@unix:~/temp$ openssl dgst -sha256 -verify codesign.pem -signature nextron-universal-installer.iso.sig nextron-universal-installer.iso
Verified OK
or in Powershell
PS C:\temp\nextron-universal-installer>Invoke-WebRequest -Uri https://www.nextron-systems.com/certs/codesign.pem -OutFile codesign.pem
PS C:\temp\nextron-universal-installer>"C:\Program Files\OpenSSL-Win64\bin\openssl.exe" dgst -sha256 -verify codesign.pem -signature nextron-universal-installer.iso.sig nextron-universal-installer.iso
Verified OK
Note
If openssl is not present on your system you can easily install
it using winget: winget install openssl.
2.5. Other Optional Requirements
2.5.1. Usage of a Reverse Proxy
If you are planing to make the Analysis Cockpit available through a reverse proxy, see Reverse Proxy to access the Analysis Cockpit.
2.6. Architecture
The following image shows an architecture overview with all products and their communication relationships.
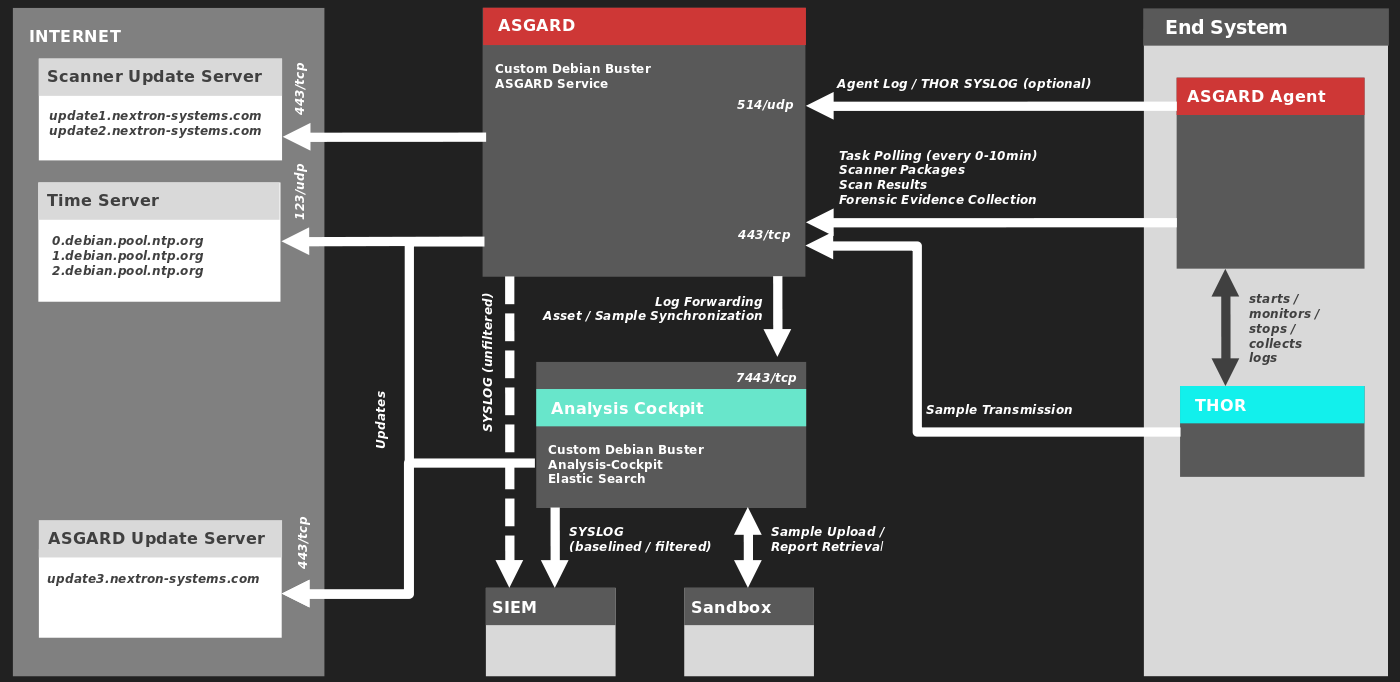
Full Architecture